New malware attack: watch out for the Windows 11 alpha attachment!
It is basically a simple, well-known recipe that attackers use to attempt to execute VBA malicious code on your computer using a supposed Windows 11 problem.
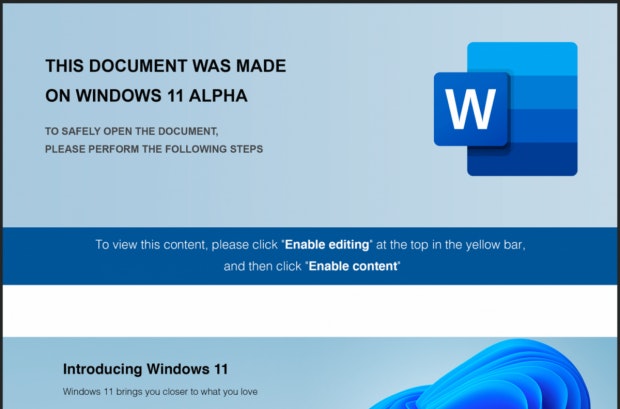
A new malware campaign is tricking users into thinking that they have to expressly allow editing of a document because it was created with the latest Windows 11 alpha version and cannot be opened otherwise. The document that the criminals send via phishing email is graphically complex and, to the untrained eye, may plausibly represent a legitimate concern.
In this way, the attackers try to gain the users’ trust. (Screenshot: Anomali / Bleeping Computer)
When attacked people try to open the document, they see the graphic element shown above, which is supposed to contain instructions on how to get to know the actual content, which could not be loaded directly due to alleged compatibility problems between Windows 11 and its predecessors. To do this, they would have to allow editing and activate the content.
People who follow this instruction from the malware senders enable the execution of VBA macros in the document. What happens then is at the discretion of the macro creator. In this case, the cybercriminals provided Microsoft Word documents with macro code, which ultimately downloads a JavaScript backdoor that the attacker can use to transfer any user data.
At this point the warning again: Never allow macros to run on Office documents!
Well-known criminal group is probably behind it
As Bleeping computer reports, security researchers at cybersecurity company Anomali believe that the campaign could be carried out by the cybercriminal group FIN7 (also known as Carbanak and Navigator), which specializes in theft of payment card data.
They came to this assessment after analyzing six such documents, they found that the installed backdoor is a variation of a payload that has been used by the FIN7 group since at least 2018.
FIN7 has been around since at least 2013, but only became known to a wider public from 2015. Some of its members have been arrested and convicted, but even after a successful blow in 2018 that arrested several members, the group appears to have remained active.
FIN7 has become known for stealing payment card data from customers of various companies. Their activities caused over a billion US dollars in damage in the United States alone. Over time, the group had succeeded in stealing more than 20 million card data records, which were processed by more than 6,500 point-of-sale terminals at around 3,600 different business locations.