Octo: an Android virus that hacks your bank account
We had already told you about Escobar and Xenomorph, two Android malware that came to pick the pockets of its poor victims, but the cases in France were not very numerous. It must be said that only certain banks were targeted. This is not the same with Octo, a malware discovered and analyzed by ThreatFabric.
The latter, fortunately not widespread on the Play Store with “only” 50,000 downloads on 2 contaminated applications, casts a wide net with around a hundred potential targets per device. As far as France is concerned, there are a lot of banking organizations (La Banque Postale, CIC, Fortuneo, BNP, Banque Populaire, LCL, Crédit du Nord, etc.), messaging applications (WhatsApp, Skype) or apps related to cryptocurrencies (Coinbase, Metamask, Binance, etc.)
#Octo Android banking #Trojan frequently mentioned on dark-web forums is in fact #ExobotCompact (#Copy) enhanced with On-Device Fraud capabilities and spread via Google Play Store. Read more details in our latest blog: https://t.co/x0ATL4642O
— ThreatFabric (@ThreatFabric) April 8, 2022
an old acquaintance
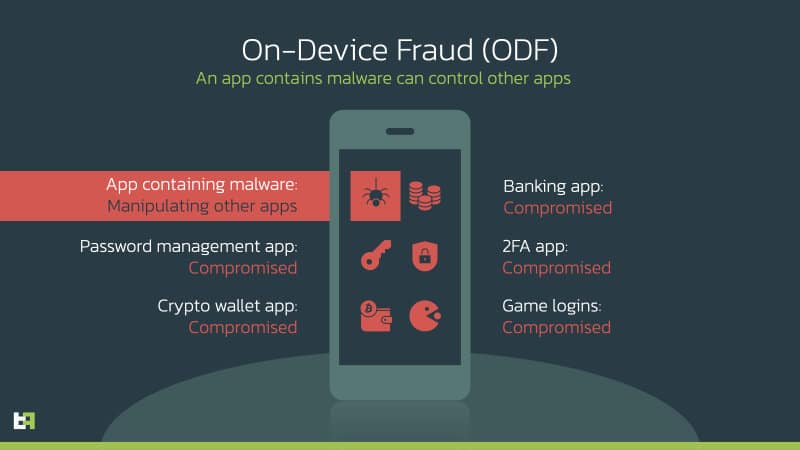
This Octo is actually a variant of Coper, itself from Exobot and ExobotCompact. And like its “illustrious” big brothers, it is a Trojan horse that allows an ODF (on-device fraud) attack where all fraudulent transactions are initiated from the same trusted device as the victim. uses every day. Once the trojan is in place, no sensitive information is safe: your usernames and passwords, your text messages (often used for double authentication), your banking application, etc.
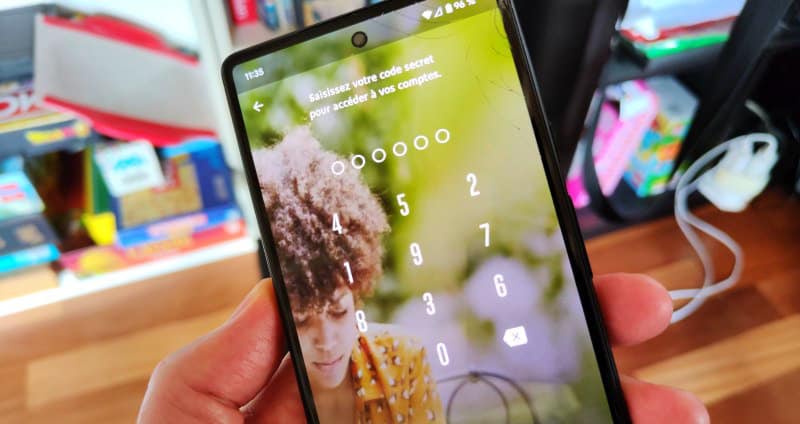
Octo disables the Play Protect function, installs a remote control module, a keylogger to record your keystrokes and it uses the native Android module to record videos of your screen. The goal is to retrieve the unique customer code used by banking applications. You know, the ones with a randomly generated number pad. Even more deceitful: the time to do all that, he lowers the brightness of the device to a minimum to go unnoticed!
The applications concerned
If you have installed Pocket Screencaster or Fast Cleaner 2021 apps from Google Play Store, chances are you are among the victims. Same with Postbank Security, Pocket Screencaster and BAWAG PSK Security apps as APKs. Be careful, this is only the tip of the iceberg since it is quite possible that other contaminated applications are still in the wild. Avoid unnecessary and little-known applications from the Play Store, do not download APK files from the Internet and even more so if you are solicited by e-mail, message or SMS.