Is your iPhone bugged? This malware spies on Apple phones!
A Russian cybersecurity giant, designer of one of the most powerful antiviruses on the market, victim of spyware. This is not the next Tom Clancy’s, but rather the recent misadventures of Kaspersky. The CEO of the company thus announced, on June 1, 2023, that some of his employees are suffering from a virus attack.
We’ve discovered a new cyberattack against iOS called Triangulation.
The attack starts with iMessage with a malicious attachment, which, using a number of vulnerabilities in iOS installs spyware. No user action is required.#IOSTriangulation pic.twitter.com/daxEYZwXwD
— Eugene Kaspersky (@e_kaspersky) June 1, 2023
A zero-click virus
The attack is said to be carried out by a malicious program called Triangulation, a Trojan horse software designed to target Apple devices. The virus, once installed on the victim’s smartphone, recovers a lot of private information: data, geolocation, but also capture of sounds and live images.
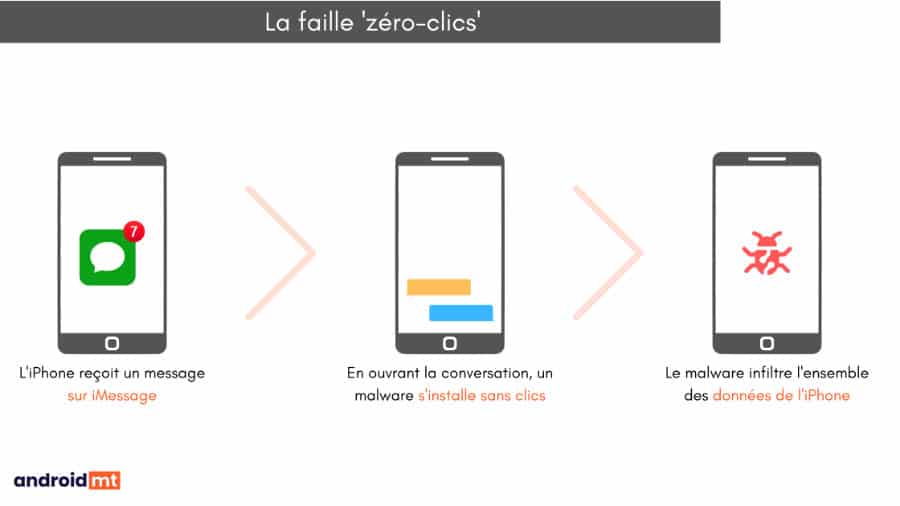
After infecting dozens of iPhones, the company identified Triangulation’s modus operandi and documented. The malware operates through a zero-click flaw from iMessage. Simply put, the targeted device receives a message containing an infected attachment that installs itself within minutes.
Russia accuses the United States
For the Russian intelligence services, there is no doubt: this attack is led by the United States, in close collaboration with Apple. For the CEO of the company, Eugène Kaspersky, the elements seem on the contrary to indicate a broader attack from iPhone users.
How to protect your iPhone?
Currently, Kaspersky has not identified a reliable and secure method to get rid of the Triangulation malware. In addition, the virus seems to disable the update of iOS, making the smartphone all the more vulnerable.
So, while waiting for a solution, the company is developing a free malware detection tool. This should make it possible to identify the presence of Triangulation as soon as a message is received, allowing the user not to open the conversation and thus avoid the zero-click flaw.


