Beware of these fake applications, they contain dangerous malware
Malware applications that hide malware are still a big problem on the Android platform, and sometimes they can break into the official Google Play store. Even more dangerous are applications that users install from unknown sources outside the official store. Portal BitDefender now alerts you to malicious applications that contain known malware Information a Flubot.
Teabot and Flubot are distributed mainly by fraudulent SMS
Both types of malware are spread via fraudulent SMS. These contain a link to download an application that pretends to be popular software. The potential victim can thus be confused with the logo and name of a well-known company or application. The malicious application, which the victim downloads via a link to a smartphone, then often allows all the permissions he requires without thinking.
With these permissions, malware can take screenshots, overlay other applications, and track the text you fill in application text boxes. Its main goal is to obtain information about your payment cards and passwords for bank accounts. The data obtained in this way is then sent to the attacker via encrypted communication.
Fake applications also copy the popular player and antivirus program
And which known applications is now copying this malware this time? For example, this is the popular VLC Player, which has over 100 million downloads in the Google Play store and is therefore trusted by many users. The original application is called VLC for Android, while the malicious version is distributed under the name VLC MediaPlayer. In addition, it has a visibly different application icon.
Attackers also copy the popular Kaspersky antivirus program among malicious applications. Another separate category are applications such as “Ad blocker”, which should be used to block ads in Internet browsers on Android smartphones. They are even more dangerous for the user because they are less visible in the system. First, they require various permissions, such as installing foreign applications, and then they are hidden in the system.
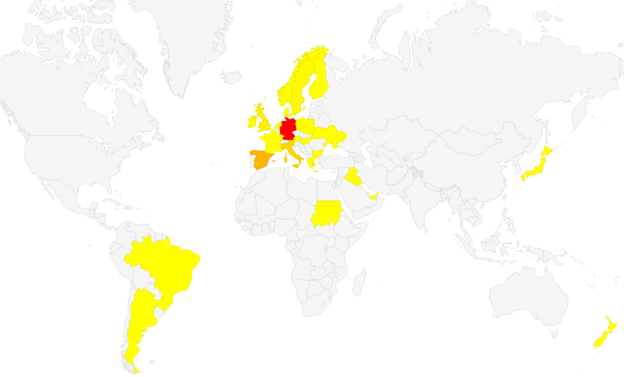
Map of countries where FluBot malware operates Photo: BitDefender.com
Map of countries where TeaBot malware operates Photo: BitDefender.com
So far, TeaBot only targets banking applications in Western and Southern Europe. Most often in Spain. Flutbot also targets institutions in Northern Europe and even South America. However, they primarily target customers of German banks. Slovak and Czech banks have not yet registered attacks on these types of malware.
Our tip
TikTok will collect biometric data from users in the US without their consent